HackTheBox | Backend Wlkathrough
Hi Folks!
Hope you are doing well.

let’s get started with enumeration.
Enumeration
Nmap Scan
nmap -T4 -v -p- -sCV <target_ip>
We got two open ports: port 22 running a SSH, port 80 running HTTP.
uvicornis a web server for hosting Python webservers.
Web Enumeration
Visiting the page returns JSON data.

It seems to be an API.
API Enumeration
Here, I used to dirsearch to fuzz the endpoints while I navigate through the returned JSON data.
dirsearch -u http://<target_ip>/
We got Unauthorized Response from /docs, so we need to find any credentials or signup.

I got another JSON data, when I accessed /api endpoint.

I acessed /api/v1 endpoint.

We’ve got two another endpoints. Let’s start with /user.

We’ve got nothing, let’s switch to /admin.

We’ve got Unauthorized Response.
So I used dirsearch again, to bruteforce /api/v1 endpoint.
dirsearch -u http://<target_ip>/api/v1/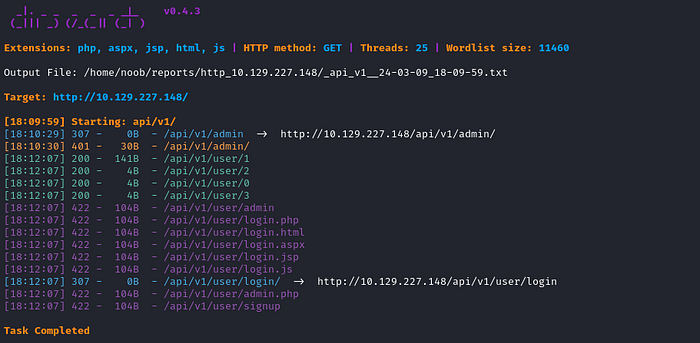
We got login endpoint and we can access users’ data.
So let’s first start with /api/v1/user/1.
When we access the user with id 1, we got admin data but we got no password.

Navigating through the other users, we got null value.
Here, I went to /api/v1/user/login to try to bruteforce the admin’s password or bypass the authentication, But it didn’t work.
So I used dirsearch again with another wordlist and I got /api/v1/user/signup endpoint.
So let’s create an account.
After a lot of errors, I was able to create an account.

Let’s login using this account.
After login time of searching and errors, I was able to login and get JWT token.
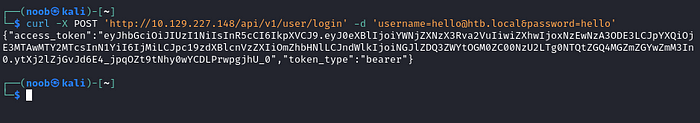
Let’s see what JWT contains. The quickest way to check is to drop it into jwt.io and see that it is a JWT.

At this time, I decided to access /docs endpoint.
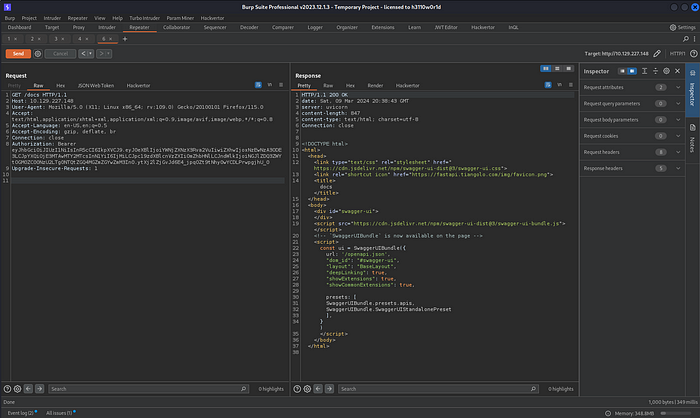
It seems that /docs endpoint is JavaScript generated.
Let’s access it on the browser, I used simple-modify-headers to add the authorization header.

Docs Enumeration
Looking through all the endpoints, they are broken into three groups (default, user, admin).

All three of admin endpoints require admin privileges, but since I have auth, I’ll give them a try. First there’s “Admin Check”.
As expected, It returns false.

Other endpoints gives permission error.
So we only have access to default and user endpoints.
User group has interesting endpoints.

First let’s access /api/v1/user/SecretFlagEndpoint and get the flag as it describes.

Let’s focus on getting access on the box.
The most interesting endpoint related to user endpoints is /api/v1/user/updatepass.
So let’s try it and change the admin’s password.
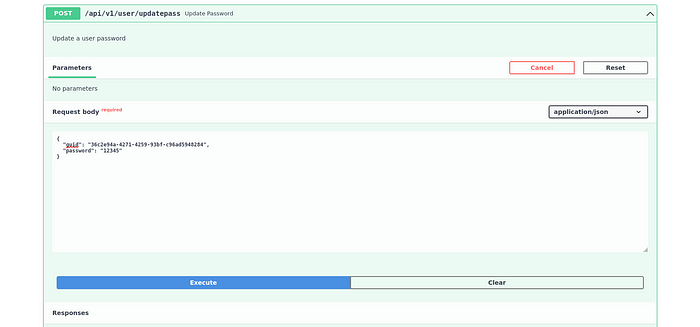
We get guid parameter from accessing /api/v1/user/1 endpoint.

We got no errors, so it seems it worked.
Let’s check it by giving the new credentials to “Authorize” button on the top of /docs endpoint.

And it seems it worked.

So let’s login with admin account.

So let’s change the authorization header with the new value and access /docs.
First, I access /api/v1/admin/ to check admin privileges.

As expected, it returns true.
So let’s access /api/v1/admin/exec/{command} to get a reverse shell.

But I got an error, Debug key missing from JWT.
It seems like we’re still missing a key to get code execution. Simply adding a "debug": true to JWT token. So we need to find the signing key of the token.
Let’s access the third admin endpoint /api/v1/admin/file to read system’s files.
I first tried with /etc/passwd and it worked.

We got just one user htb. I tried to access /home/htb/.ssh/id_rsa, but I got an error.
So here I tried to read processes variables from /proc/self/environ to get the home directory of the running API to read the source code.

We got APP_MODULE=app.main:app and PWD=/home/htb/uhc.
That says the working directory is /home/htb/uhc, and that the app is located likely in app/main.py.
So let’s read it.

From reading the imported files, we can get the application’s files and paths.
So let’s first try to read /api/v1/admin/exec/{command} endpoint, to make sure our previous assumptions are true.
From reading /home/htb/uhc/app/api/v1/api.py, we got /api/v1/admin endpoint source code file location /home/htb/uhc/app/api/v1/endpoints/admin.py.
So let’s read it.

At the end of the file, we got the source code of exec function.
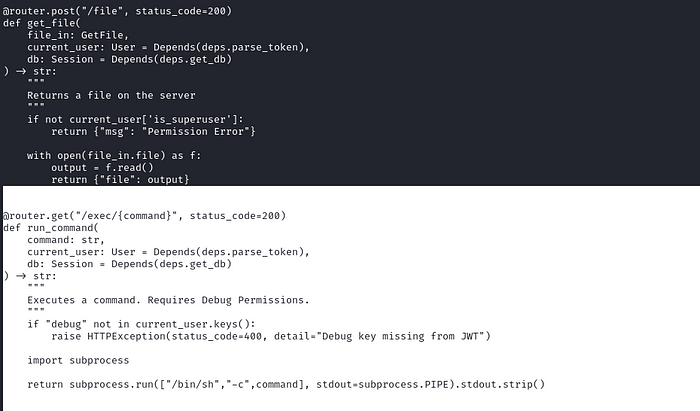
As we expected before, It needs "debug": true to be added to JWT token.
So let’s return back and get the signing key from /home/htb/uhc/app/core/config.py.

Now, let’s add the debug key.

Lateral Movement
Access the Box
Let’s use the modified token and check /api/v1/admin/exec/{command} again.

After I worked without any problems, let’s get a access on the box.

Shell

Checking the uhc directory, we got .git directory and auth.log is mostly set up for the application logs.

First, I tried to get git logs by running git log, but git wasn’t installed.
Root
So I decided to read auth.log and I got an interesting activity, does not seem to be a username as there’s just one user on the box.
I decided to try to switch to root using the found “password” and It worked!!

Conclusion
This was great fun!
I hope you enjoyed the walkthrough. I waiting for your feedbacks.
Don’t forget to check other walkthroughs.









