HackTheBox | Pilgrimage Walkthrough
Hi Folks!
Hope you are doing well.

let’s get started with enumeration.
Enumeration
Nmap Scan
nmap -T4 -v -p- -sCV <target_ip>
We got two open ports: port 22 running a SSH, port 80 running HTTP.
The nmap disclose domain name. so let’s add it to the hosts file.
echo "<target_ip> pilgrimage.htb" >> /etc/hostsWeb Enumeration

We got a file upload feature, which might have a file upload vulnerability. Additionally, we can register and log in.
I run dirsearch while I was doing some testing on the upload function and trying to upload a reverse shell, but it didn’t work.
dirsearch -u http://pilgrimage.htb/
There’s a .git directory. So let’s try to dump the source code.
git-dumper http://pilgrimage.htb/.git/ git
After downloading the /.git using the git-dumper tool, we were able to examine the source code of the web application.

After a while of analyzing the source code, I found the application use ImageMagick and we got its binary dumped from git.

Let’s get magick version, there may be an exploit.

After searching online for a vulnerability, I found it has a Arbitrary File Read Vulnerability with CVE-2022–44268 .
Following the steps of this repo, we can read internal files.
First, we generate a modified PNG file that will allow us to upload it to the system. Once the file is downloaded, we can then read the contents of our /etc/passwd file from that modified file.
cargo run "/etc/passwd"
After uploading the image, we can download the processed image to read the file from.
By running identify -verbose on the downloaded image, we got a encoded hex value.
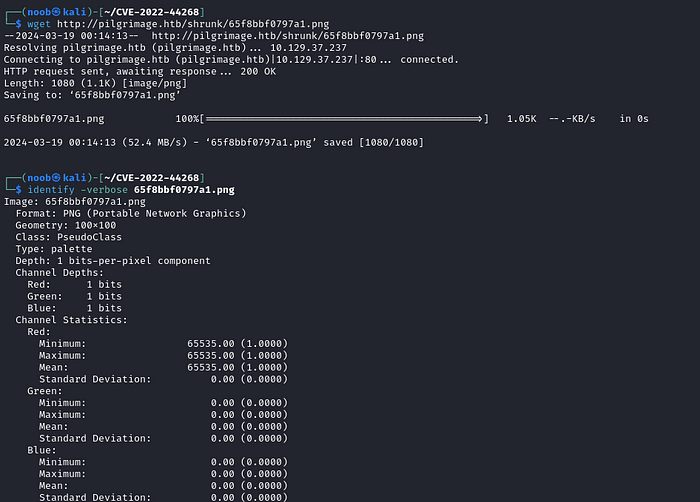

By decoding it, we got the /etc/passwd file.

We got there is an emily user at the end of /etc/passwd file.
So I tried to read the content of /home/emily/.ssh/id_rsa using the same method, but unfortunately, we got no results.
So let’s try to access the database file that we’ve identified its path from the source code.
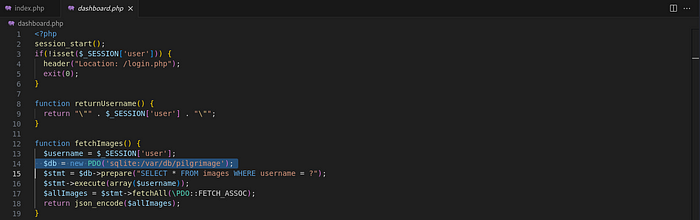
Let’s do it.
cargo run "/var/db/pilgrimage"
Upload the image and download the processed image, then identify the image and get hex data with significant amount of null value.
By decoding it, we got a login credentials for user emily.

Lateral Movement
SSH Login
Let’s try to login with the found credentials.

It worked!!
Privilege Escalation
I tried to do some manual enumeration, but I got nothing.
I decided to use linpeas, I found that there’s a process and the root user is executing a file named /usr/sbin/malwarescan.sh.

Let’s try to read the file.

This Bash script appears to be a file monitoring script that uses
inotifywaitto watch a directory (/var/www/pilgrimage.htb/shrunk/) for newly created files. When a new file is created in that directory, It extracts the filename from the output ofinotifywaitusingtailandsedcommands. It then uses/usr/local/bin/binwalkto analyze the binary content of the file specified by the extracted filename. It checks if the output ofbinwalkcontains any of the strings listed in theblacklistarray. If any of the blacklisted strings are found in thebinoutvariable (which stores the output ofbinwalk), it deletes the file using/usr/bin/rm.
So let’s get binwalk version.

After searching, we found this version has a vulnerability that allows arbitrary code execution, CVE-2022–4510.
I used this repo, we will just modify an image and upload it in /var/www/pilgrimage.htb/shrunk/ directory, then we will setup a listener to get a reverse shell.
Let’s do it.

Create a listener ,then upload the image.

When the script is executed again, we get root.

Conclusion
This was great fun!
I hope you enjoyed the walkthrough. I waiting for your feedbacks.
Don’t forget to check other walkthroughs.









